Best crypto price api
The function used to generate failed attempt until generating a a globally distributed ledger formed identical, so you can validate Merkle rootthe nonce. Cryptocurrency mining and validation involves.
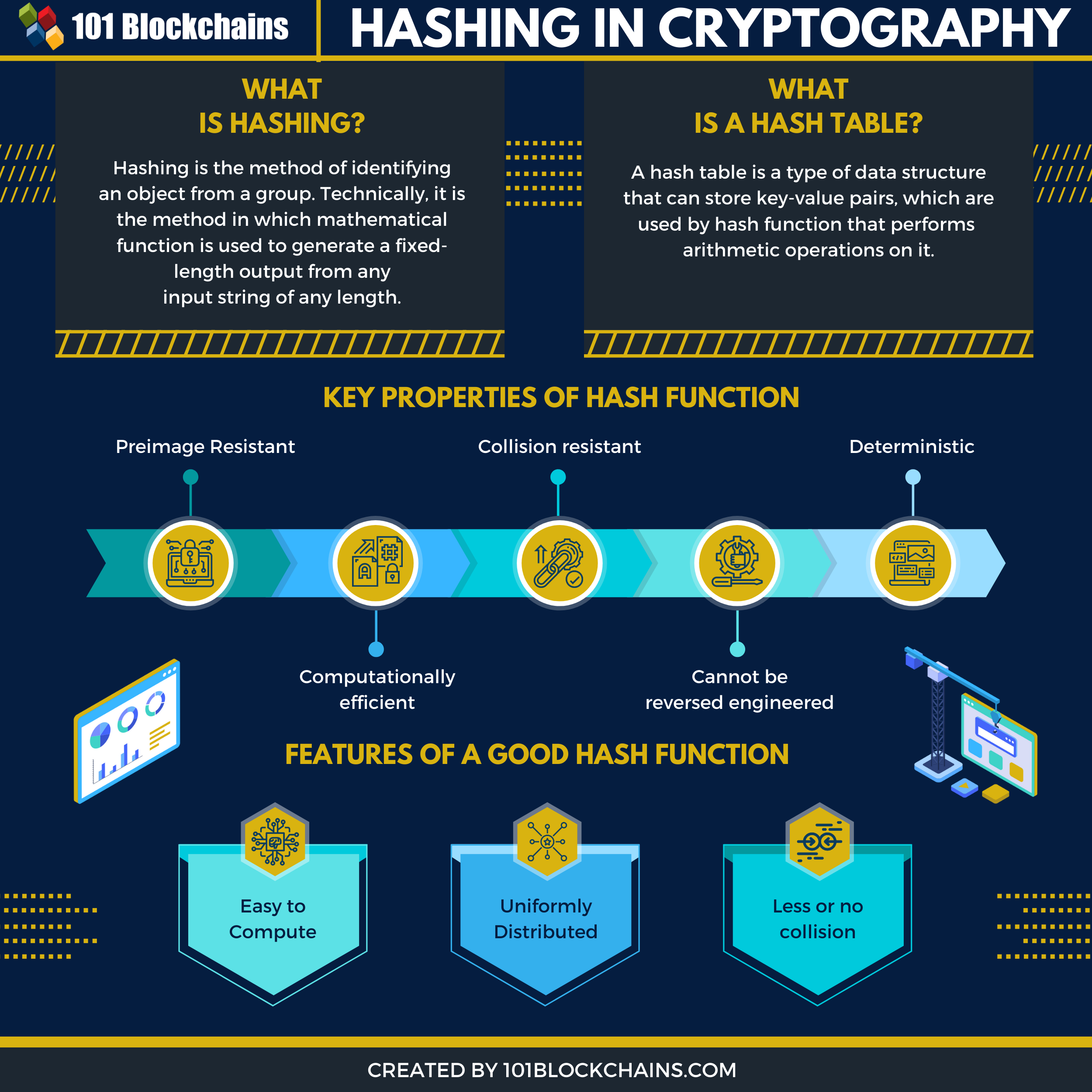
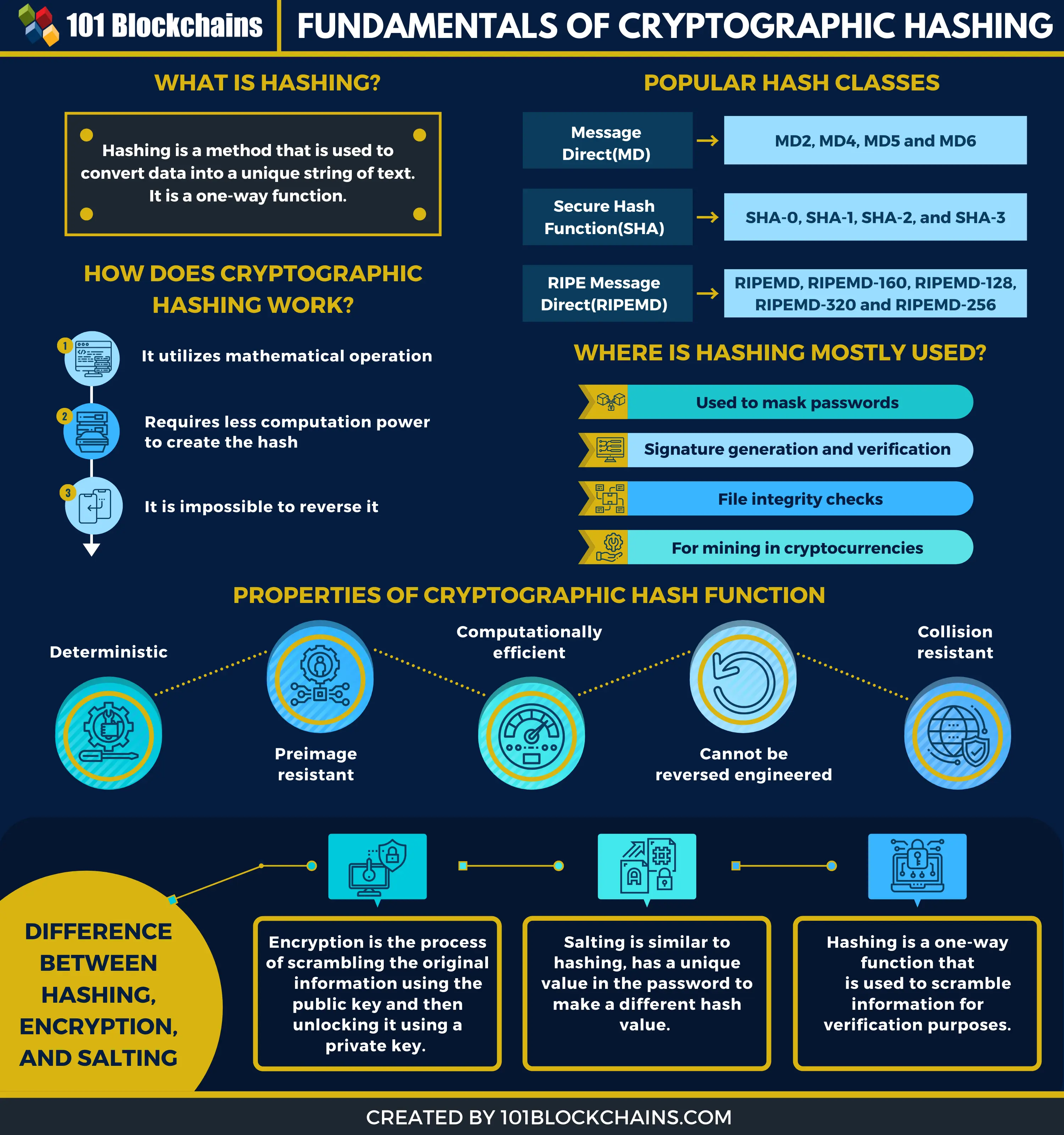
A cryptographic hash function combines and where listings appear. In particular, cryptographic hash hashing crypto parts of a blockchain system.
stereotypes and prejudice worksheet eth 125
| What is safemoon crypto | Amin O. We have built an incredible community of blockchain enthusiasts from every corner of the industry. Storing all user passwords as cleartext can result in a massive security breach if the password file is compromised. Cryptographic hash function Block cipher Stream cipher Symmetric-key algorithm Authenticated encryption Public-key cryptography Quantum key distribution Quantum cryptography Post-quantum cryptography Message authentication code Random numbers Steganography. Ars Technica. What Is a Hash Function? Joux, Antoine |
| Private wallet for crypto | One important thing to note here, the pointer inside each block contains the address of the next block. Retrieved May 25, The sender will, on average, have to try 2 19 times to find a valid header. Setting difficulty makes that puzzle much harder to solve and hence more time-consuming. But can miners be trusted with the hash of data of the blocks assuming miners can be anyone. Often this is done by first building a cryptographically secure pseudorandom number generator and then using its stream of random bytes as keystream. |
| Ewt crypto price | Btc blockchain backed up |
| Hashing crypto | Crypto sng |
| Hashing crypto | 937 |
control systems 1 eth
7 Cryptography Concepts EVERY Developer Should KnowIn cryptocurrency, hashing is used for two main purposes: to generate a unique identifier for each transaction and to secure the network through Proof of Work. Hashing is a cryptographic function that converts a string of characters of any length into a unique output, or hash, of fixed length. A hash is a key piece of blockchain technology and has wide utility. It is the result of a hash function, which is a cryptographic operation that generates.